Introduction
In recent years, manufacturers supplying products to the Department of Defense (DoD) have encountered a dramatic increase in the numbers of counterfeit components in the supply chain. In most cases, counterfeits are devices that have been re-marked with false information as to their origin, age, content, or capability; and many are found to be entirely nonfunctional. Because the true age, specifications, and/or functions of such devices are unknown, the effects of age and stress on the devices are also unknown, meaning the results of the reliability models and/or reliability testing originally used to establish product reliability are no longer relevant. Aside from affecting reliability, counterfeit components could also compromise the safety of equipment.
A suspected reason for the growing number of counterfeiting incidents is insufficient control of the supply chain, which is due in part to manufacturers’ increased reliance on outsourced, off-shore manufacturing, subcontractors, and even procurement [1 2]. Although component obsolescence may also be a factor, the vast majority of counterfeit components are fake versions of genuine devices that are still in production. Whatever the cause, counterfeit components have infiltrated product manufacturing, most notably in equipment vital to the U.S. national defense, thereby jeopardizing equipment reliability and safety.
The Cost of Counterfeiting
Although there is not a singular definition of a counterfeit component, the Aerospace Industries Association defines it as a “product produced or altered to resemble a product without authority or right to do so, with the intent to mislead or defraud by presenting the imitation as original or genuine [3].”
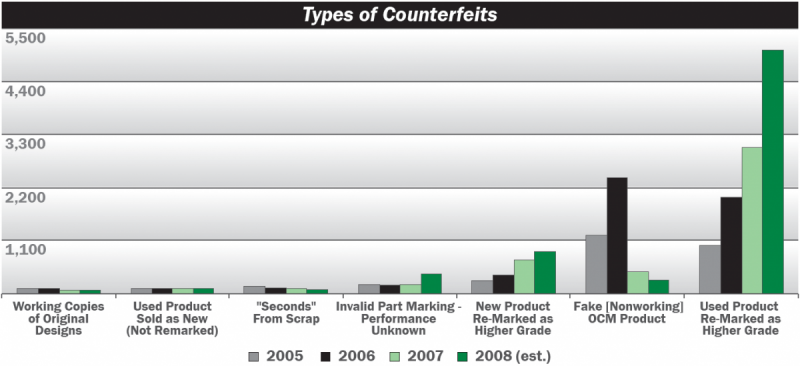
A study performed by the Department of Commerce’s Bureau of Industry and Security found that, in the DoD supply chain alone, the number of known counterfeit incidents rose from approximately 3,300 in 2005 to more than 8,000 in 2008 [3]. An alternate survey funded by the U.S. Navy increased the counts of incidents to 3,868 and 9,356 for the same two years. Further, experts estimate that the confirmed counterfeit incidents represent only a small portion of the actual number of occurrences, some of which go undetected, unreported, or misidentified as simply “bad parts.” So how extensive is the problem?
- In 2002, the FBI estimated that U.S. businesses lose between $200 billion and $250 billion per year to product counterfeiting; about 7% of that amount is in electronics. No doubt, the problem has only continued to grow since that estimation.
- In 2010, approximately 46% of component manufacturers and 55% of integrated circuit (IC) manufacturers surveyed reported that they have encountered counterfeit versions of their products [4].
- From November 2007 to May 2010, U.S. Customs made more than 1,300 seizures (representing 5.6 million semiconductors) with trademarks of approximately 100 actual companies.
Whether procured through brokers, Internet sales, or even “trusted” distributors, fake components are appearing in a wide variety of DoD-related equipment, in everything from aircraft to helicopters and submarines [5]. These components have included the following:
- 75 parts in the Identification Friend Foe (IFF) system [1].
- 1,500 parts in the production and repair of the A9 missile’s printed circuit assemblies [6].
- 350 parts in the beam steering control of the Navy Cobra Replacement Program [6].
- $16 million worth of counterfeit ICs sold from China and Hong Kong to U.S. Navy/defense contractors [6].
- Counterfeit IC memories in U.S. Missile Defense Agency mission computers (Lockheed Martin) for Terminal High Altitude Area Defense (THAAD) missiles. The cost to fix the problem was $2.7 million [5].
- ICs in Hercules C-130J that were actually used 1990s Samsung devices, recycled and remarked by a company in China. And according to Samsung, “it is not possible to project the reliability” of used parts [5].
- An estimated 15% of spare and replacement parts for DoD equipment are counterfeit [7].
Clearly, ICs seem to be a prime target for counterfeiting in electronics (as shown in Figure 1); however, manufacturers have also identified many other counterfeit component parts, such as wire, resistors, capacitors, inductors, connectors, fuses, relays, and virtually every major component type.
Counterfeiting Methods
Figure 2 indicates some of the major types of counterfeiting methods that are affecting the country’s electronic supply chains.
Figure 2: Counterfeit Part Methods.
The primary methods currently employed to counterfeit DoD components include the following.
Remarking – Real components, new or used, functional or nonfunctional, are re-marked with false information, such as any of the following: the manufacturer, function (part number), date code, lot number, country of origin, quality level, performance grade, and package style. For many IC types, “blacktopping” (the application of a thin layer of epoxy or other colorant) is used to first obscure the original device markings; then the new or modified markings are applied (see Figure 3). Although earlier instances of blacktopping were visually evident, counterfeiters have become more sophisticated, making visual detection more difficult. In addition, there have been occurrences in the past where re-marking was purposely performed by the actual manufacturer. Although this practice is relatively rare, it can further complicate the task of distinguishing genuine parts from fakes. Thus, communication with the original manufacturers is essential to aid in detecting fake parts.

Figure 3: A Partially “Blacktopped” and Stamped Part With a False Identification Code. Part Number indicates a CLCC Package, but This Package Is a CDP. (NASA)
Sometimes the device may not even provide the function that its markings indicate. In the instance shown in Figure 4, the outer packaging identifies the component as an operational amplifier, but the die markings inside indicate the actual, and different, function. Such a problem is not visually apparent. X-ray inspection could detect such problems, although functional testing would, in this case, have been a more economical means of discovering this fake.
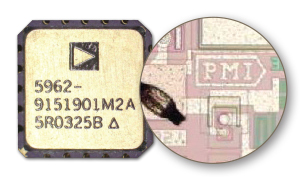
Figure 4: A Part with Falsified Function Markings. The Markings (left) Indicate an Op Amp From ADI, but the Part Contains Die from a Voltage Reference From PMI (right).
Reuse – Used components sold as new are perhaps the largest category of counterfeit devices. Electronics recycling has given rise to an influx of used components, primarily from mainland China, through brokers or other dubious outlets [2, 3, 4, 5, 8]. China imports used/scrap electronics and (using low-cost labor) removes devices from the discarded circuit boards. Such parts later bear re-markings (date code, lot, device type, quality level, etc.) and are returned to the marketplace. And military equipment is a prime target for such devices, as MIL-spec components are increasingly difficult to find and/or have long lead times.
Figure 5 shows the metal leads of supposedly new components that bear the obvious signs of previous assembly to a printed circuit board.

Figure 5: “New” Circuit Board Leads Showing Evidence of Prior Assembly and Use. (Courtesy of NASA)
Unauthorized Production – With so many IC houses, IC fabrication is often outsourced. In addition, several manufacturing facilities that produce genuine parts have been found also to have made unauthorized versions of those components, which were then sold through another outlet. These components may have been overruns that may or may not have undergone proper testing or were fallouts that did not meet specification and should have been scrapped. Although the number of these reported incidents has been minimal so far, the devices’ genuine appearance (even under X-ray) means that identifying such parts can be extremely difficult, and may easily go undetected. And even when these devices fail, the failure may be misidentified as a random failure of a genuine part.
False Approval Markings – Agency approvals or listing markings are usually required when product safety or compliance with a standard (such as Underwriters Laboratories [UL], Conformance European [CE], Canadian Standards Association [CSA], Federal Communications Commission [FCC], etc.) is required. Because obtaining and maintaining approvals can be costly, unscrupulous manufacturers may skip the required approval process, yet will claim compliance and apply false markings. Target devices in this category typically include fuses, wiring (insulation), switches, relays, and circuit breakers. The various approvals and listings help to ensure safe operation of a product, so false approval markings represent a potential safety hazard to the user.
In all of these examples, the counterfeit part likely has a different or degraded function than that of a genuine part. Counterfeit parts often bear several of the previously listed abnormalities, with many of them being both used and re-marked. At best, counterfeit parts can increase the failure rate of a product in an unpredictable manner. At worst, counterfeit parts can malfunction and create a safety hazard.
Security
Most of the public attention related to counterfeit electronics has been associated with re-marking and reusing devices. Another area of potentially greater security concern is the possibility of inserting trojan circuits, especially into programmable devices. Such circuits could steal information and relay it to an “enemy,” or they could, on command or “randomly,” prevent the device from operating as designed. Unlike software viruses or trojans, hardware-based equivalents are much more difficult to detect and could be impossible to “patch” or defeat. Researchers have demonstrated how “backdoors” into supposedly secure programmable devices (field programmable gate arrays [FPGAs]) could be exploited to insert such circuit functions [9]. Another security concern is the potential for copying complex programmable devices. Many articles have been written on this subject, and many FPGA and microprocessor manufacturers have offered additional means of ensuring the security of their devices [10 11 12]. Whether designers will take full advantage of these security measures remains to be seen.
Countermeasures to Counterfeiting
One possibility for helping to differentiate between genuine parts and counterfeits in the future is to include a form of unique marker on genuine parts. The U.S. Defense Advanced Research Projects Agency (DARPA) Supply Chain Hardware Integrity for Electronics Defense (SHIELD) program proposed such a solution with an item called a dielet. Such a device could contain an encryption engine and sensors to detect tampering and could be affixed to components, either by the manufacturer or after the fact, without affecting the device’s functionality. Although the proposal did not garner immediate support, in early 2015 DARPA issued a pair of contract awards, one to Northrop Grumman Corp and another to Draper Labs, specifically to develop robust dielets [13]. The keys to this solution will be low manufacturing cost and, to be completely effective in combating counterfeits, adoption by all major manufacturers.
Image Courtesy of the U.S. Navy
A similar initiative uses botanical DNA ink technology in the device package to provide positive identification of device authenticity. Developed by Applied DNA Sciences, which is working with the Defense Logistics Agency (DLA), a DNA-embedded ink (SigNature DNA) provides a marker that reportedly cannot be altered or copied. As with the dielets, the DNA markers are initially targeted for use with larger microcircuits, such as microprocessors, FPGAs, and memories [14].
Another partial solution, developed by SRI International under DARPA’s Integrity and Reliability of Integrated Circuits (IRIS) program, is an Advanced Scanning Optical Microscope (ASOM) designed for the Navy to aid in the forensic analysis of ICs that are suspected of being counterfeits. ASOM uses a narrow infrared laser beam to scan a device down to nanometer levels to reveal details of device construction. ASOM presently appears to be a one-off design (not yet a standard product) and is likely quite expensive at this time. IRIS also has a goal of developing IC test methods and diagnostics to characterize the reliability of devices via testing small sample sizes based on the current understanding of physics-of-failure (PoF) mechanisms.
Other detection methods include chemical testing for blacktopping, the use of X-ray fluorescence and spectroscopy techniques, as well as parametric and functional testing [15].
While dielets and/or DNA markers could certainly aid in combating future counterfeits, virtually all investigations into the problem of counterfeit electronics have concluded that tighter control of procurement processes and the supply chain is the best immediate solution. While China is the source of the majority of counterfeit components, China did not cause the problem. A DoD investigation identified a number of inadequacies in processes of equipment manufacturers that led to lax control of their supply chain and components, opening the door that allowed counterfeits to be assembled into products.
Based on the Society of Automotive Engineers (SAE) International Standard AS5553A [16], the recently passed Defense Federal Acquisition Regulation Supplement (DFARS) Case 2012–D055 recommends the following process improvements aimed at combating and eliminating counterfeit components in products. While the recommendations are aimed at suppliers to the DoD, they are also good practices for any organization (manufacturer and service) that wishes to avoid counterfeits. They apply to confirmed counterfeits as well as suspected fake devices. The key to combating counterfeiting is to design, operate, and maintain a system to detect/avoid counterfeits. This includes:
- Training personnel to avoid, identify, and report counterfeits.
- Flowing down requirements (through the supply chain) for counterfeit detection/avoidance.
- Ensuring that only original manufacturer sources, or suppliers that obtain parts exclusively from such sources, are used.
- Maintaining traceability of all components throughout the supply chain, and keeping informed of counterfeiting information and trends.
- Instituting procedures to identify counterfeit parts. This task can be extremely challenging as both false positives and false negatives are commonplace, even with seasoned inspectors. Affordable, commercial equipment is necessary.
- Inspecting/testing parts with appropriate pass/fail inspection criteria. Again, there are no hard and fast rules that will be 100% accurate; thus, building a knowledge/example base is essential.
- Continually reviewing databases, the Government-Industry Data Exchange Program (GIDEP) reports, and other sources of counterfeiting information (e.g., NASA, ERAI, Independent Distributors of Electronics Association [IDEA], etc.).
- Reporting and quarantining counterfeit parts.
- Controlling obsolete parts.
For guidance as to general processes for ensuring that components are genuine, refer to IDEA-STD-1010B [17] and Components Technology Institute (CTI) Counterfeit Components Avoidance Program (CCAP) 101.
Finally, the new International Organization for Standardization (ISO) 9000-2015 standard due to be released in late 2015 will include an emphasis on risk assessment as related to a company’s practices [18]. Certainly, one of the risks to consider is that of encountering counterfeit components when an organization decides to outsource its manufacturing, procurement, or service activities or to adopt other practices that could compromise the traceability of components. Embracing ISO 9000-2015 could help companies make careful, well-informed decisions about their business practices and avoid risky practices that could jeopardize the reliability and safety of the products they manufacture.
While the suggested solutions would admittedly place a greater burden on both component and original equipment manufacturers (OEMs), these solutions should help manufacturers and service organizations to regain control of the supply chain and proactively root out counterfeits. And this control will help ensure that products consist only of genuine parts as defined by the design documentation and that the product design will be able to maintain the prescribed reliability and safety requirements.
For additional information on counterfeit device data and avoidance methods, the following resources are recommended:
Data
- NASA QLF Web Site
- GIDEP
- ERAI Counterfeit Parts Notifications
Guidance and Technical
- CTI-CCAP-101
- IDEA-STD-1010B [17]
- SAE AS5553A [16]
- DFARS Case 2012–D055, Federal Register 48 CFR Parts 202, 231, 244, et al., Defense Federal Acquisition Regulation Supplement [19]
- DARPA ‐BAA‐14‐16 SHIELD Program
- DARPA IRIS Program.
References:
- Livingston, Henry. “Securing the DOD Supply Chain from the Risks of Counterfeit Electronic Components.” BAE Systems Electronic Solutions, 2010.
- Harda, Lawrence. “Semiconductor Technology and U.S. National Security.” U.S. Army War College, Carlisle Barracks, PA, April 2010.
- Aerospace Industries Association of America, Inc. “Counterfeit Parts: Increasing Awareness and Developing Countermeasures.” 2010.
- Crawford, Mark, et al. “Defense Industry Base Assessment: Counterfeit Electronics.” U.S. Department of Commerce, January 2010.
- Levin, Carl, et al. “Inquiry Into Counterfeit Electronic Parts in the Departments of Defense Supply Chain.” Committee on Armed Services, U.S. Senate, May 2012.
- Machen, Ronald. “Owner and Employee of Florida-based Company Indicted in Connection With Sales of Counterfeit High Tech Devices Destined to the U.S. Military and Other Industries.” Press Release, U.S. Department of Justice, September 14, 2010.
- Toohey, Brian. “Counterfeit Semiconductors – A Clear and Present Threat.” Testimony Before Senate Committee on Armed Services, Counterfeit Electronic Parts in the U.S. Military Supply Chain, November 8, 2011.
- Pecht, Michael, and Len Zuga. “Counterfeit Electronics and the China Connection.” CALCE Electronic Products and Systems Center, University of Maryland, SMT Magazine, April 2012.
- Skorobogatov, Sergei, and Christopher Woods. “Breakthrough Silicon Scanning Discovers Backdoor in Military Chip.” University of Cambridge, Computer Laboratory, Cambridge, UK; Quo Vadis Labs, London, UK, International Association for Cryptologic Research, 2012.
- Altera Corp. “An FPGA Design Security Solution Using a Secure Memory Device.” 2007.
- Gwon, Youngjune L., et al. “DISTROY: Detecting Integrated Circuit Trojans with Compressive Measurements.” Harvard University, 2012.
- Bhasin, Shivam, et al. “Hardware Trojan Horses in Cryptographic IP Cores.” Institut MINES-TELECOM, TELECOM-ParisTech; Secure-IC S.A.S., FDTC, Santa Barbara, CA, 2013.
- Keller, John. “Northrop Grumman Joins Draper Lab in Program to Combat Military Counterfeit Electronics.” Military and Aerospace Electronics, http://www.militaryaerospace.com/articles/2015/01/northrop-darpa-shield.html, January 2015.
- Reece, Beth.“Combating Counterfeits.” http://www.dla.mil/Loglines/Pages/LoglinesJF2013Story07.aspx, Defense Logistics Agency, 2013.
- Guin, Ujjwal, et al. “Counterfeit Integrated Circuits: A Rising Threat in the Global Semiconductor Supply Chain.” Proceedings of the IEEE, vol. 102, no. 8, August 2014.
- Society of Automotive Engineers (SAE) International. “Counterfeit Electronic Parts; Avoidance, Detection, Mitigation, and Disposition.” SAE Standard AS5553A, January 2013.
- Independent Distributors of Electronics Association (IDEA). Acceptability of Electronic Components Distributed in the Open Market. IDEA-STD-1010-B, 2011.
- Isazada, Natella. “ISO 9000:2015 – New Era in Quality Management?” http://pw21.startlogic.com/wp/2014/10/03/iso-90002015-new-era-in-quality…, ASQ Vancouver, October 2014.
- Defense Acquisition Regulations System. “Detection and Avoidance of Counterfeit Electronic Parts.” Defense Federal Acquistion Regulation Supplement, Final Rule, DFARS Case 2012-D055, May 2014.