an email newsletter released every month highlighting the latest articles, events, technical inquires, and voices from the community
Threat Evaluation and Weapon Allocation/Assignment (TEWA) Algorithms
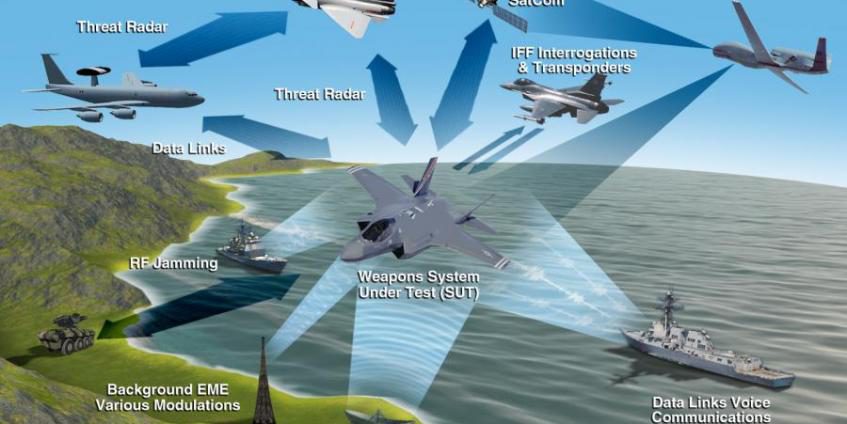
http://www.edwards.af.mil/Portals/50/images/772/141205-F-ZZ999-101.jpg?ver=2016-06-23-105719-640 / (Image Credit: Edwards Air Force Base)
Posted on May 3, 2018 | Completed on April 16, 2018 | By: Travis J. Kneen
What research has been done on threat and weapon assessment, evaluation, and analysis?
DSIAC was asked for research papers, journals, and points of contact relevant to threat evaluation and weapon assignment (TEWA) algorithms to assist in the development of algorithms to assign threat values to hostile targets. DSIAC compiled bibliographies utilizing open sources and the DTIC R&E Gateway, a list of relevant subject matter experts (SMEs), and contacted a publisher to acquire research papers of interest not found in the searched sources. The full set of responses were delivered to the inquirer.
Want to find out more about this topic?
Request a FREE Technical Inquiry!

